publications
welcome to the secret publications page
2020
-
 Mnemosyne: An Effective and Efficient Postmortem Watering Hole Attack Investigation SystemJoey Allen, Zheng Yang, Matthew Landen, Raghav Bhat, Harsh Grover, Andrew Chang, Yang Ji, Roberto Perdisci, and Wenke LeeIn Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, Virtual Event, USA, 2020
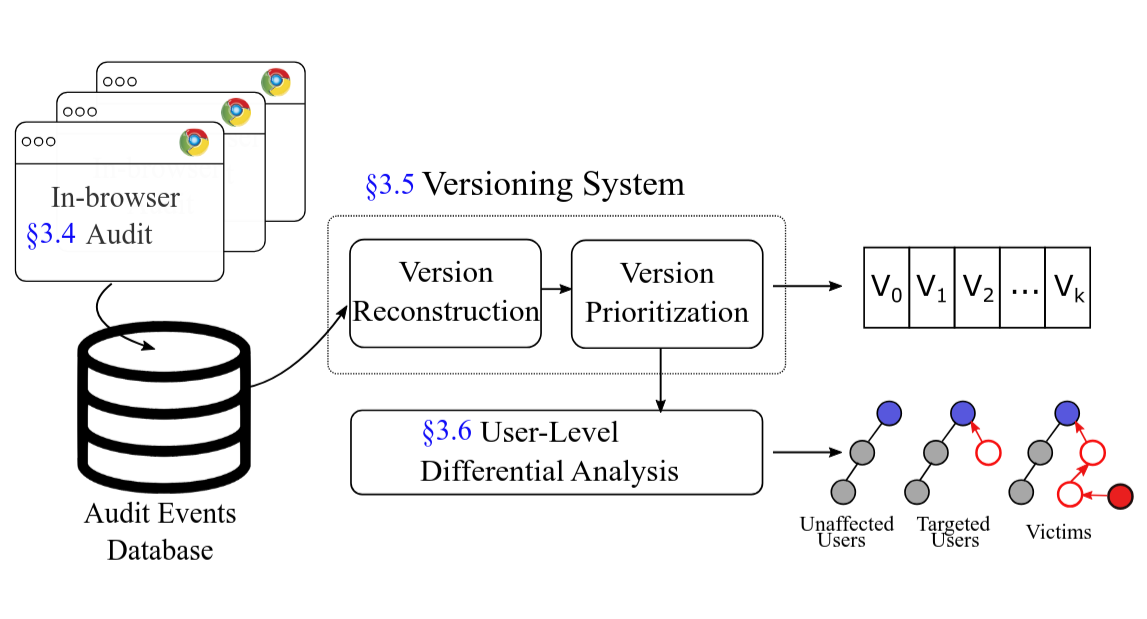
Mnemosyne: An Effective and Efficient Postmortem Watering Hole Attack Investigation SystemJoey Allen, Zheng Yang, Matthew Landen, Raghav Bhat, Harsh Grover, Andrew Chang, Yang Ji, Roberto Perdisci, and Wenke LeeIn Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, Virtual Event, USA, 2020Compromising a website that is routinely visited by employees of a targeted organization has become a popular technique for nation-state level adversaries to penetrate an enterprise’s network. This technique, dubbed a "watering hole" attack, leverages a compromised website to serve as a stepping stone into the true victims’ network. Despite watering hole attacks being one of the main techniques used by attackers to achieve the initial compromise stage of the cyber kill chain, there has been relatively little research related to detecting or investigating complex watering hole attacks. While there is existing work that seeks to detect malicious modifications made to an otherwise benign website, we argue that simply detecting that the website is compromised is only the first stage of the investigation. In this paper, we propose Mnemosyne, a postmortem forensic analysis engine that relies on browser-based attack provenance to accurately reconstruct, investigate, and assess the ramifications of watering hole attacks. Mnemosyne relies on a lightweight browser-modification-free auditing daemon to passively collect causality logs related to the browser’s execution. Next, Mnemosyne applies a set of versioning techniques on top of these causality logs to precisely pinpoint when the website was compromised and what modifications were made by the adversary. Following this step, Mnemosyne relies on a novel user-level analysis to assess how the malicious modifications affected the targeted enterprise and seeks to identify exactly which employees fell victim to the attack. Throughout our extensive evaluation, we found that Mnemosyne’s forensic analysis engine was able to identify the true victims in all seven real-world watering hole scenarios, while also reducing the amount of manual analysis required by the forensic analyst by 98.17% on average.